Squirro Roles & Permissions#
To control access to different parts of a Squirro installation, Squirro provides different roles, each with its own unique set of permissions.
There are two primary levels of roles and permissions within Squirro:
Server-level roles
Project-level roles
This page describes how server and project roles and permissions are assigned and managed.
Important
People must first be added at the server level before they can be added to a project. You cannot give a person access to a project without first adding them to that project’s server.
Cluster Permissions#
There is a third level of permissions, Cluster, that only applies to Squirro Self-Service instances. For an overview of Cluster roles and permissions, including mapping to server roles, see Cluster Roles and Permissions for Self-Service.
Server-Level Permissions#
At the server level, there are three roles:
Administrator: The top-level permission role able to perform all functions.
User: Able to view projects they’ve been added to and connect to them via API. Can also create new projects.
Restricted: Read-only access to the server.
Note: There is a deprecated role called Demo that can be ignored.
Roles and their associated permissions are outlined in the table below:
Permissions |
Administrator |
User |
Restricted |
|---|---|---|---|
View projects they’ve been added to |
|||
Change their My Account information |
|||
Access instance API information |
|||
Create new projects |
|||
Access the Server Space |
|||
Access the Squirro Monitoring Space |
Two Ways People Can Be Added to the Server#
How users are added to your server depends on whether or not your Squirro installation utilizes Single Sign-On (SSO).
If your instance has enabled SSO, then users may only be added through the configured third-party SSO provider.
Note: After a person is authenticated via SSO for the first time, they are created in the Squirro Server space.
If your project does not use SSO, then users may be added via the Server → Users page.
Setting Up SSO#
If you are looking to set up SSO (SAML) for Squirro, see SAML SSO for Squirro.
Configuring Roles and Permissions via SSO#
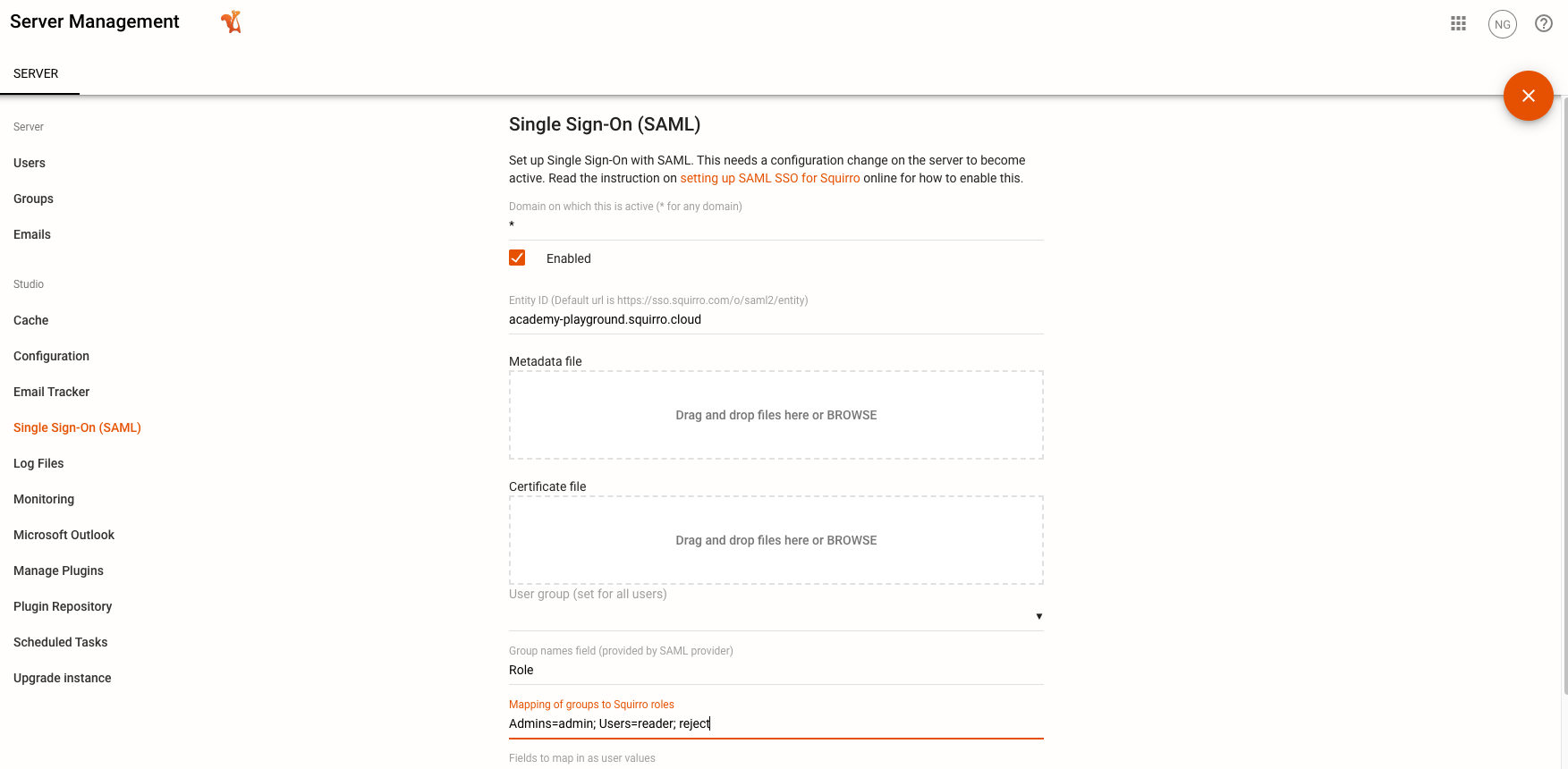
You can manage role assignments through the Single Sign-On (SAML) menu option within the Server space.
To do so, follow the steps below:
Log in to your Squirro installation as a server administrator.
Navigate to the Server space.
Click Single Sign-On (SAML) in the left menu.
Use the Mapping of groups to Squirro roles field to assign permissions as shown in the screenshot below:
Notes for administrators
When SSO is enabled, the role mapping configuration is the source of truth for server-level roles. Manual role changes made through the Squirro UI are temporary and reset when the user logs in again.
Squirro recommends disabling UI user management so that user provisioning is managed exclusively by your identity provider (IdP). See the Enabling and Disabling UI User Management page.
Adding People and Managing Roles and Permissions With SSO Disabled#
If your installation does not use SSO, follow the steps below to add users or manage roles and permissions via the Squirro UI:
Log in to your Squirro installation as a server-level Administrator.
Navigate to the Server space.
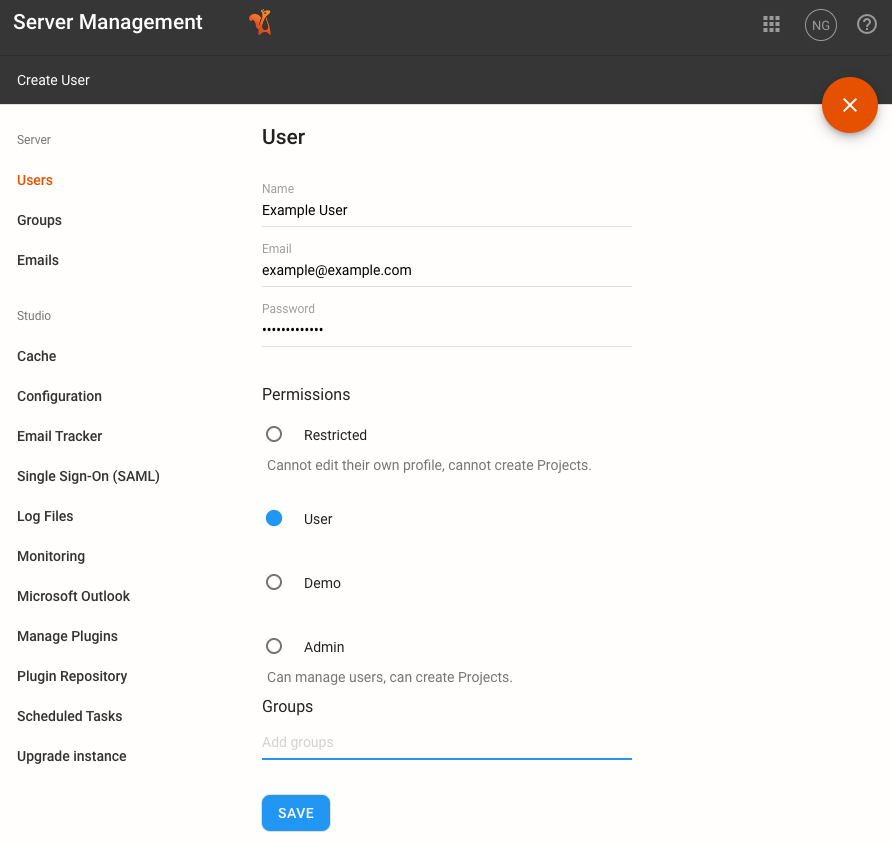
Click Users in the left menu.
Click the plus icon to add a new user and assign roles (as shown in screenshot below) or hover over an existing user and click Edit to modify their details.
Squirro Monitoring#
Only server-level Administrators have access to Squirro Monitoring, which serves as the central activity and data ingestion log monitoring hub for all projects on a Squirro installation.
Project-Level Permissions#
At the project level, there are three roles:
Administrator
Member
Reader
Note
There is also an Owner role that shares the same permissions as the Administrator role, but only applies to the person who created the project. There is no functional difference between the two roles.
Roles and their associated permissions are outlined in the table below:
Permissions |
Administrator |
Member |
Reader |
|---|---|---|---|
Read items |
|||
Manage sources |
|||
Manage dashboards |
|||
Manage saved searches |
|||
Access the Setup Space |
|||
Manage project members |
|||
Delete project |
The Member role has access to most Setup space features. It does not, however, have access to most items within the Settings tab.
The project-level Administrator role has Setup space permission levels halfway between a Member and a Server Administrator. The project-level Administrator can view more Settings than the Member, but it cannot see the Studio settings managed by server-level administrators.
Note
If you require Readers to change the fields of an Items widgets (which they cannot do by default), enabling topic.item.allowed-reader-edit-keywords will permit them to do so. You can find this setting by navigating to Setup → Settings → Project Configuration.
Reader Permission for Read and Bookmarked State#
Users with the Reader role receive special permissions that allow them to track reading progress and bookmark items without granting full item update capabilities. The Reader role includes the following permissions by default:
items.write.update.read_state
Allows Readers to mark items as read or unread and track personal reading history.
items.write.update.starred_state
Allows Readers to bookmark items by adding them to collections. This permission name reflects the legacy starred system. The permission now enables adding items to the Bookmarks collection and other personal collections.
These permissions do not grant the ability to modify item content, metadata, or other properties. They apply only to the read state and collection membership. Administrator and Member roles receive the broader items.write.update permission, which includes these capabilities plus full item modification rights.
The Reader role permissions are defined in the platform configuration and cannot be modified through the user interface.
For detailed information about read and bookmarked items functionality, see the Read, Unread, New, and Bookmarked Items page.
Groups#
Important
Groups are created on the server level in the Server space, but their permissions are applied at the project level in the Setup space under Settings → Project Members.
Groups are a useful (and recommended) tool for managing user permissions, particularly if your project uses SSO.
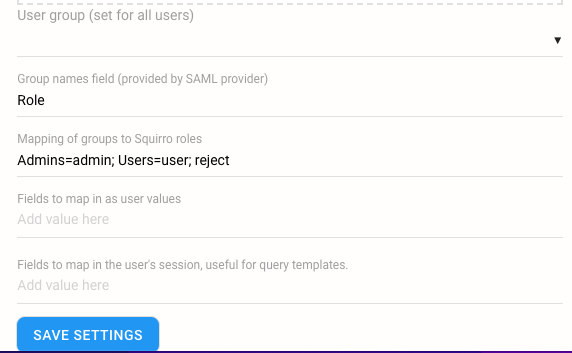
Under the Single Sign-On (SAML) configuration option within the Server space, you can map Squirro roles by group using the Group Names Field based on their roles/groups in the SSO identity provider (IdP), as shown in the screenshot below:
Dashboard Permissions#
In addition to the roles and permissions outlined on this page, you can also restrict access to individual project dashboards under the Setup > Visualization space.
To learn more, see Dashboard Permissions.
